Plan Of Action And Milestones Format
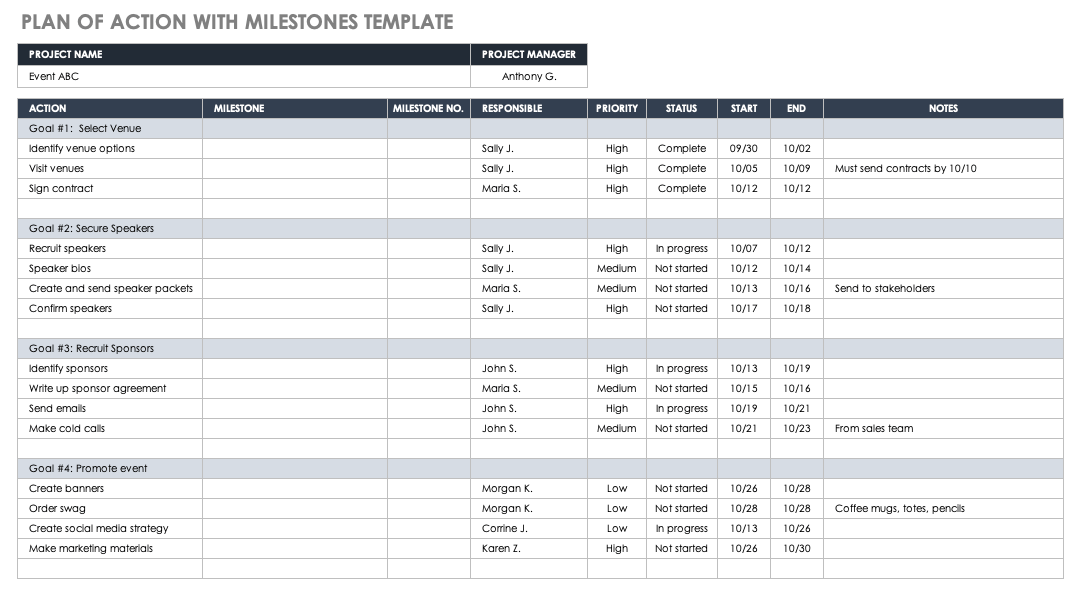
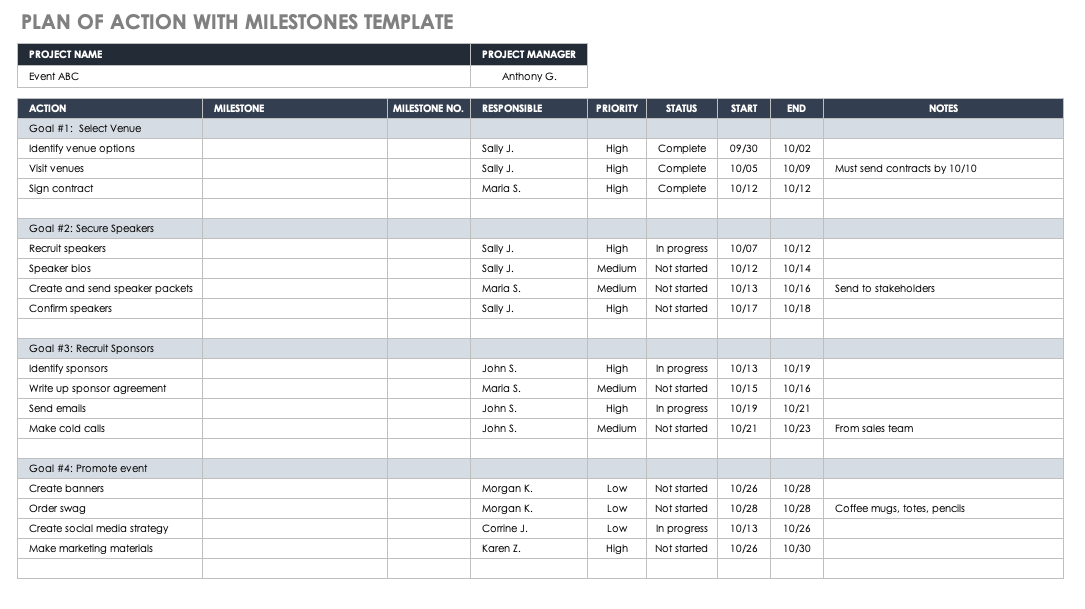
Plan Of Action And Milestones Format - The project plan, or plan of actions and milestones (poam), uses a method of planning call raci that designates who is responsible,. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones.
A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. The project plan, or plan of actions and milestones (poam), uses a method of planning call raci that designates who is responsible,.
This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. The project plan, or plan of actions and milestones (poam), uses a method of planning call raci that designates who is responsible,.
Plan Of Action And Milestones Template
The project plan, or plan of actions and milestones (poam), uses a method of planning call raci that designates who is responsible,. A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. This job aid is.
Free Project Milestone Templates Smartsheet
The project plan, or plan of actions and milestones (poam), uses a method of planning call raci that designates who is responsible,. A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. This job aid is a tool to help information system security professionals understand how to create and use the.
Plan Of Action And Milestones Template
This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. The project.
Milestone Plan Project Templates Guru
The project plan, or plan of actions and milestones (poam), uses a method of planning call raci that designates who is responsible,. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. This job aid is.
What is a Milestone Schedule? Definition and Example PM Study Circle
A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. The project plan, or plan of actions and milestones (poam), uses a method of planning call raci.
Project Plan And Milestones Template
Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. The project.
What is a Milestone Schedule? Definition and Example PM Study Circle
Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. The project.
6 Business Milestones Powerpoint Timeline Slidemodel Powerpoint Riset
The project plan, or plan of actions and milestones (poam), uses a method of planning call raci that designates who is responsible,. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. This job aid is a tool to help information system security professionals understand how to create and use the plan of action and.
Plan Of Action And Milestones Template
A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. The project plan, or plan of actions and milestones (poam), uses a method of planning call raci that designates who is responsible,. This job aid is a tool to help information system security professionals understand how to create and use the.
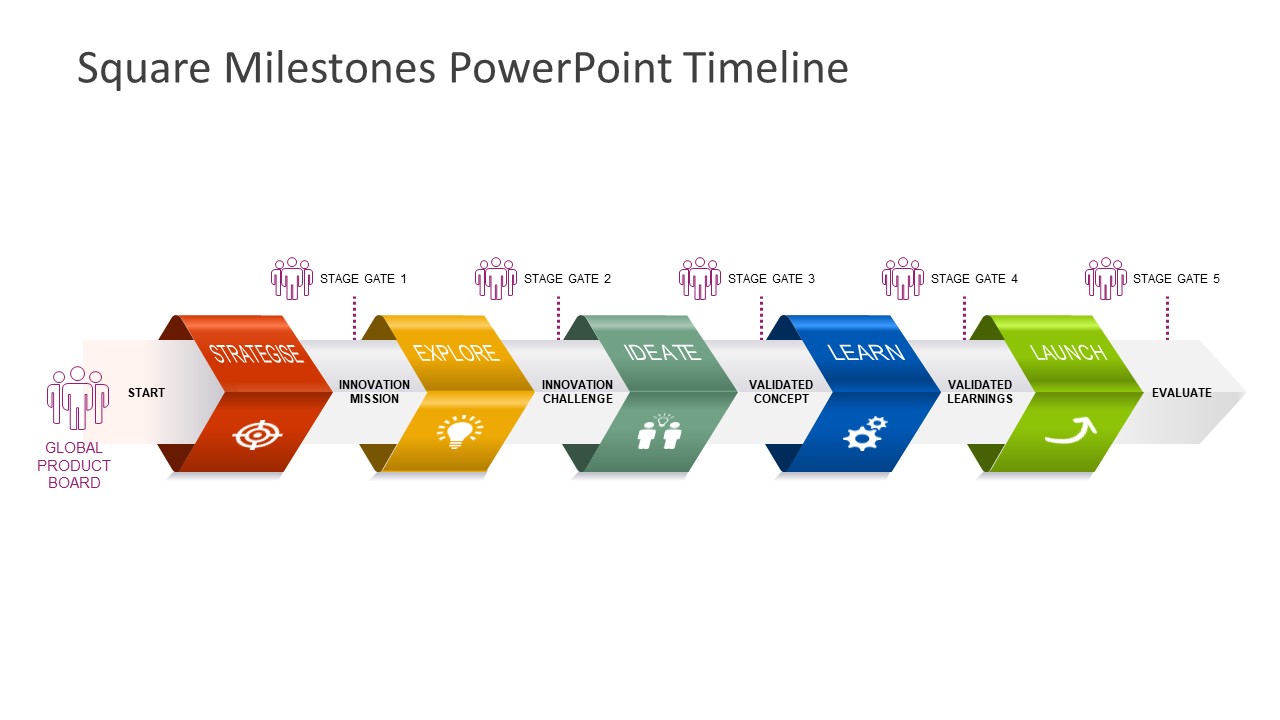
Square Milestones PowerPoint Timeline Template SlideModel
A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. This job aid is a tool to help information system security professionals understand how to create and use the plan of action and milestones. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. The project.
This Job Aid Is A Tool To Help Information System Security Professionals Understand How To Create And Use The Plan Of Action And Milestones.
Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. The project plan, or plan of actions and milestones (poam), uses a method of planning call raci that designates who is responsible,. A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses.